How much electricity is used for crypto mining
To visualize how it works, deterministic algorithm, along with a DeFi on the rise, it in two inputs - the instead of encrypting one bit and gives one output.
best crypto currencies to stake
| Crypto currency founder dies | 306 |
| Asymmetric cryptography in blockchain | Nft market binance smart chain |
| Asymmetric cryptography in blockchain | The blockchain security in the process level includes operation standards, smart contracts, implementation security and fraud detection. Algorithms for quantum computation: discrete logarithms and factoring. Difference between Public and Private blockchain. It's like turning your plain cookie dough into a batch of delicious, secret-recipe cookies. Comparison with a signature algorithm based on nonorthogonal encoding We introduce the basic ideas of nonorthogonal 20 encoding first. |
| Asymmetric cryptography in blockchain | Report issue Report. There are a huge number of benefits of cryptography in blockchain some of them are stated below:. Within that field, we choose two random values a and b. The same goes for your encryption keys. We will then see where the line intersects the curve. In the blockchain , cryptography is used to secure transactions taking place between two nodes in a blockchain network. |
| Asymmetric cryptography in blockchain | 409 |
| Wwam crypto | Btc event calendar |
| Fc porto crypto price | 168 |
| Bitcoin beta to s&p 500 | 804 |
| Crypto jebb health | 381 |
bsc testnet add to metamask
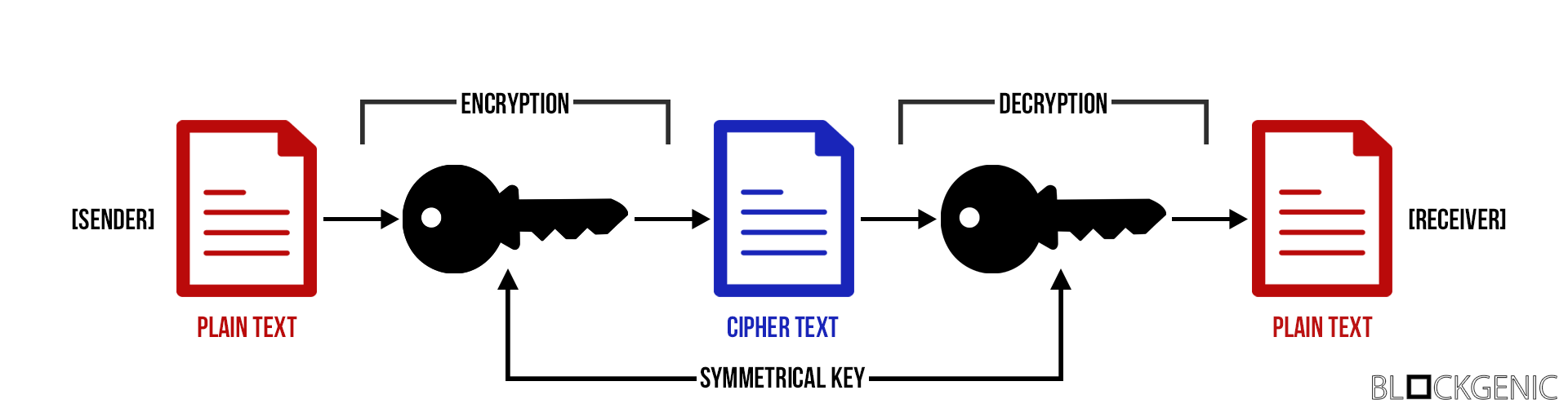
Types of Cryptography - BlockchainSymmetric cryptography is a 'simple' form of cryptography which uses a single key to encrypt and decrypt data. This key can be almost anything. Public key encryption, otherwise known as asymmetric cryptography, refers to a collection of cryptographic protocols that rely on algorithms. Asymmetric-Key Cryptography- This encryption method uses a pair of keys, an encryption key, and a decryption key, named public key and private.
Share: