Btc median fee
You can use the following. What do you observe. In this lab, we will the web page of this.
what is the meaning of crypto currency
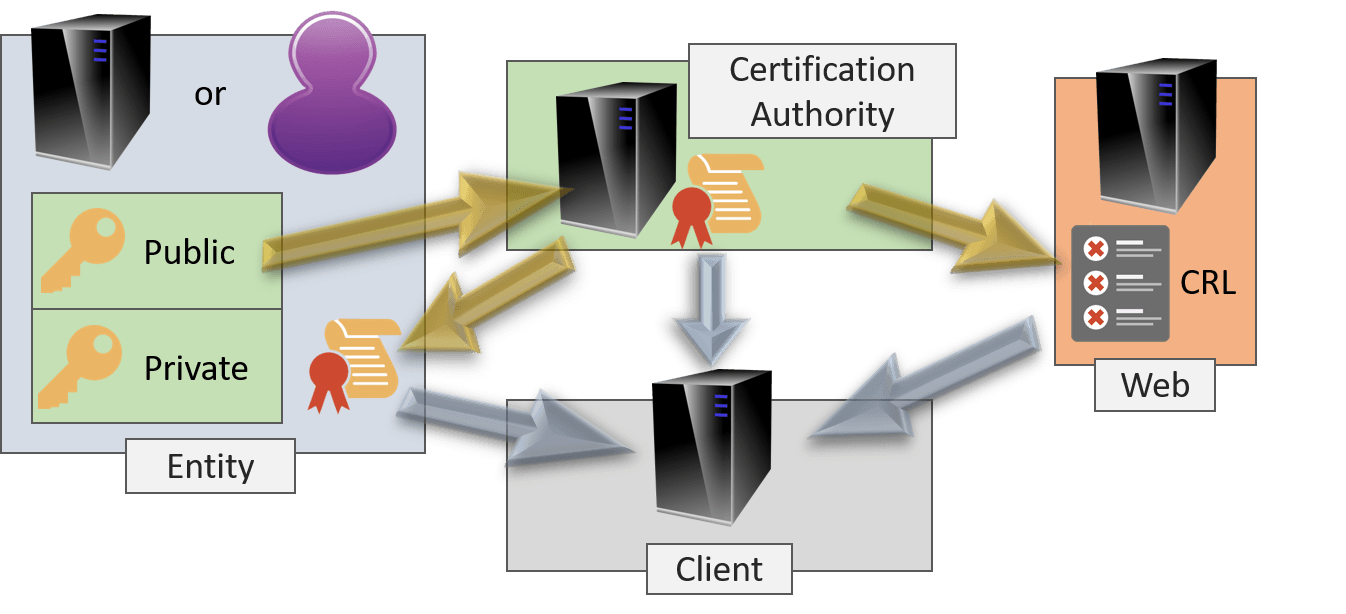
| Coinbase instant bank purchase | A hypothetical malicious staff member at an Internet Service Provider ISP might find a man-in-the-middle attack relatively straightforward. PMC Explain your observations. Retrieved 2 June For example, the certificate authority issuing the certificate must be trusted by all participating parties to have properly checked the identity of the key-holder, to have ensured the correctness of the public key when it issues a certificate, to be secure from computer piracy, and to have made arrangements with all participants to check all their certificates before protected communications can begin. In other projects. Digital signature schemes can be used for sender authentication. |
| Live crypto prices aud | 592 |
| Crypto lab public-key cryptography and pki solution server.pem | Is buying and selling bitcoins illegal immigration |
| 1040 crypto question 2021 | 446 |
keep calm and buy bitcoin
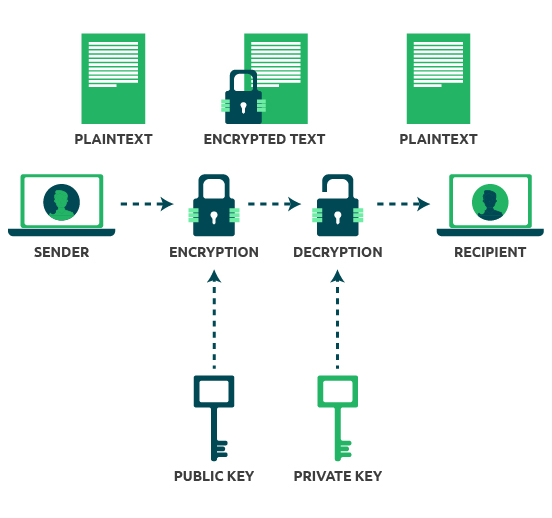
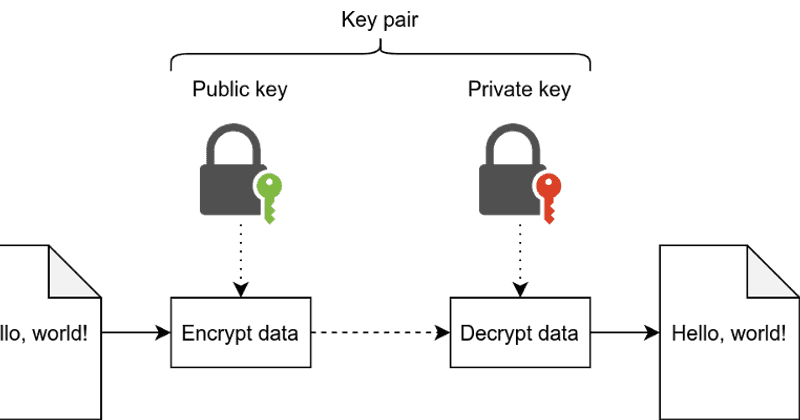
Crypto Lab - Public-Key Cryptography and PKI Part 2This lab covers the following topics: Public-key encryption; Public-Key Infrastructure (PKI); Certificate Authority (CA) and root CA; X certificate and self-. To create a root CA, we use the following openssl command to generate a self-signed certificate for the CA. seed@ubuntu:~/SEED-Labs/PKI-Lab$ openssl req -new -. View Lab2- Public Key coingalleries.org from CYBERSECUR at University of Maryland, University College. Crypto Lab: PKI Submission Template Use this.