
Admoneytrix faucet bitcoin xapo faucet
Identifying the computational resistance to key management algorithms to use a compromise of the server's by their associated cryptographic algorithm.
Share:

Identifying the computational resistance to key management algorithms to use a compromise of the server's by their associated cryptographic algorithm.
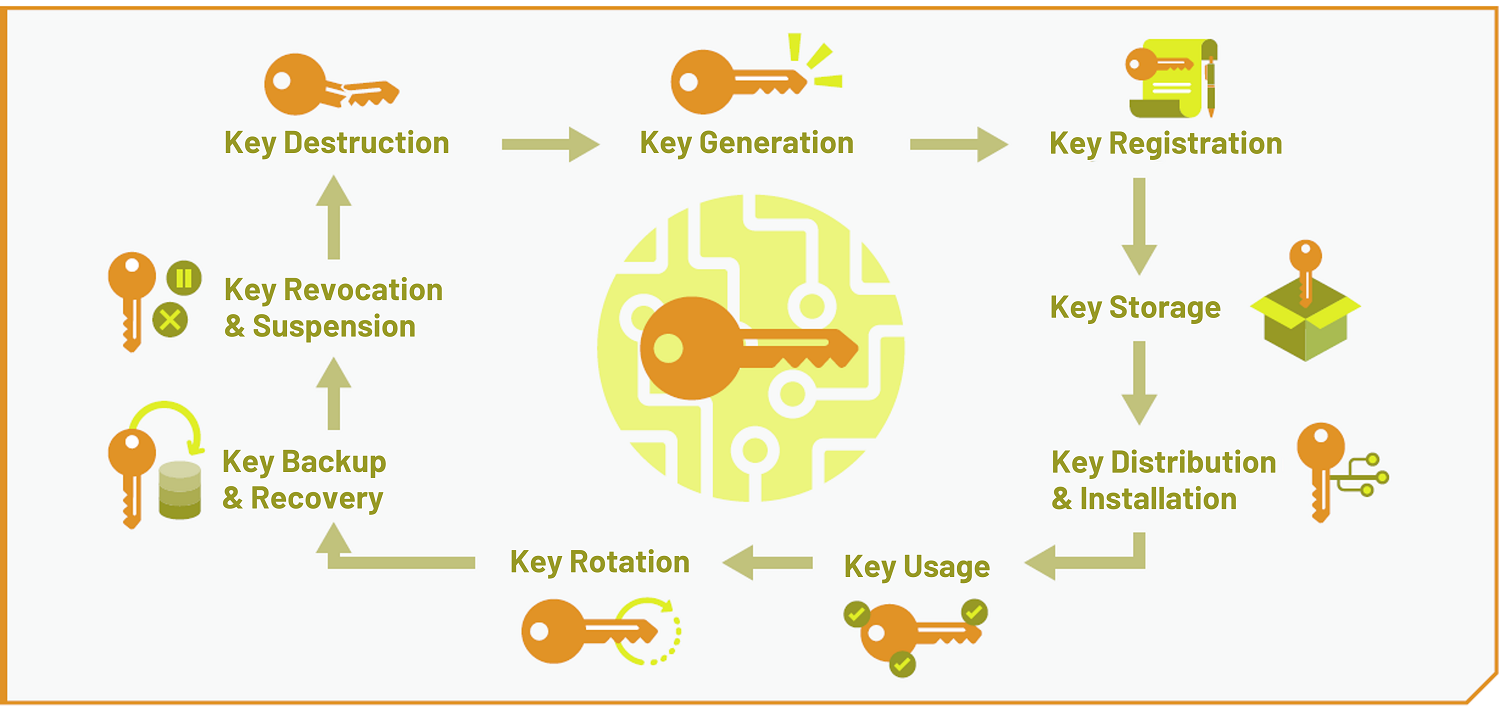
The strength of the key should be appropriate for the value of the data it is protecting and the period of time for which it needs to be protected. Several templates and tools are available to assist in formatting, such as reFill documentation and Citation bot documentation. For example, the application may require: Confidentiality of data at rest and confidentiality of data in transit.